|
|
| (36 revisões intermediárias por 2 usuários não estão sendo mostradas) |
| Linha 1: |
Linha 1: |
| − | =PAGINA DE TESTES=
| |
| | | | |
| − | =Configurações DNS= | + | =Acesso Externo WEB= |
| | | | |
| − | num-threads: <number>
| + | ==IP > Firewall > Nat== |
| − | The number of threads to create to serve clients. Use 1 for no threading.
| |
| | | | |
| | + | '''Para adicionar clique no botão:''' ([[Arquivo:MikrotikBotaoAdd.png|link=]]) |
| | | | |
| − | edns-buffer-size: <number>
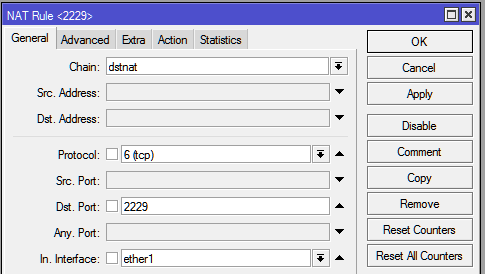
| + | *'''Aba General >''' |
| | + | **'''Chain: '''dstnat |
| | + | **'''Protocol: '''tcp |
| | + | **'''Dst. Port: '''8080 |
| | + | **'''In. Interface: '''ether1 (Interface de Entrada de LINK) |
| | | | |
| − | Number of bytes size to advertise as the EDNS reassembly buffer size. This is the value put into datagrams over UDP towards peers. The actual buffer size is determined by msg-buffer-size (both for TCP and UDP). Do not set higher than that value. Default is 4096 which is RFC recommended. If you have fragmentation reassembly problems, usually seen as timeouts, then a value of 1480 can fix it. Setting to 512 bypasses even the most stringent path MTU problems, but is seen as extreme, since the amount of TCP fallback generated is excessive (probably also for this resolver, consider tuning the outgoing tcp number).
| + | <div class="img-responsive align-center">[[Arquivo:MikrotikIpFirewallNatAccExt1.png|link=]]</div> |
| | | | |
| | | | |
| − | msg-buffer-size: <number>
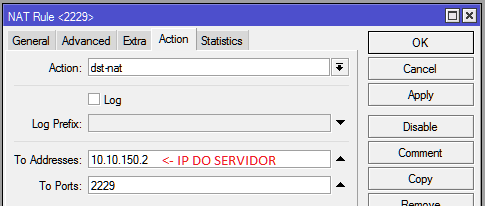
| + | *'''Aba Action>''' |
| | + | **'''Action: '''dst-nat |
| | + | **'''To Address: '''10.10.150.2 (IP do Speedr) |
| | + | **'''To Ports: '''8080 |
| | | | |
| − | Number of bytes size of the message buffers. Default is 65552 bytes, enough for 64 Kb packets, the maximum DNS message size. No message larger than this can be sent or received. Can be reduced to use less memory, but some requests for DNS data, such as for huge resource records, will result in a SERVFAIL reply to the client.
| + | <div class="img-responsive align-center">[[Arquivo:MikrotikIpFirewallNatAccExt2.PNG|link=]]</div> |
| | | | |
| | | | |
| − | msg-cache-slabs: <number>
| + | '''Regras''' |
| | + | /ip firewall nat |
| | + | add action=dst-nat chain=dstnat comment="SPEEDR - EXTERNO WEB" dst-port=8080 in-interface=\ |
| | + | ether1 protocol=tcp to-addresses=10.10.150.2 to-ports=8080 |
| | | | |
| − | Number of slabs in the message cache. Slabs reduce lock contention by threads. Must be set to a power of 2. Setting (close) to the number of cpus is a reasonable guess.
| + | =Acesso Externo SSH= |
| | | | |
| | + | ==IP > Firewall > Nat== |
| | | | |
| − | jostle-timeout: <msec>
| + | '''Para adicionar clique no botão:''' ([[Arquivo:MikrotikBotaoAdd.png|link=]]) |
| | | | |
| − | Timeout used when the server is very busy. Set to a value that usually results in one roundtrip to the authority servers. If too many queries arrive, then 50% of the queries are allowed to run to completion, and the other 50% are replaced with the new incoming query if they have already spent more than their allowed time. This protects against denial of service by slow queries or high query rates. Default 200 milliseconds. The effect is that the qps for long-lasting queries is about (num- queriesperthread / 2) / (average time for such long queries) qps. The qps for short queries can be about (numqueries-perthread / 2) / (jostletimeout in whole seconds) qps per thread, about (1024/2)*5 = 2560 qps by default.
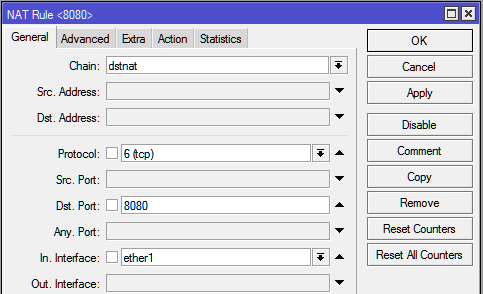
| + | *'''Aba General >''' |
| | + | **'''Chain: '''dstnat |
| | + | **'''Protocol: '''tcp |
| | + | **'''Dst. Port: '''2229 |
| | + | **'''In. Interface: '''ether1 (Interface de Entrada de LINK) |
| | | | |
| − | rrset-cache-size: <number>
| + | <div class="img-responsive align-center">[[Arquivo:MikrotikIpFirewallNatAccExt3.png|link=]]</div> |
| | | | |
| − | Number of bytes size of the RRset cache. Default is 4 megabytes. A plain number is in bytes, append 'k', 'm' or 'g' for kilobytes, megabytes or gigabytes (1024*1024 bytes in a megabyte).
| |
| | | | |
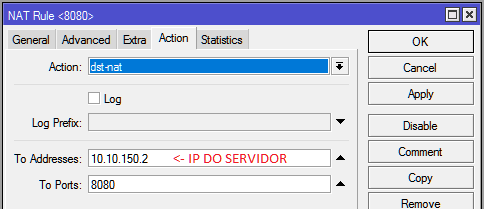
| | + | *'''Aba Action>''' |
| | + | **'''Action: '''dst-nat |
| | + | **'''To Address: '''10.10.150.2 (IP do Speedr) |
| | + | **'''To Ports: '''2229 |
| | | | |
| − | cache-max-ttl: <seconds>
| + | <div class="img-responsive align-center">[[Arquivo:MikrotikIpFirewallNatAccExt4.png|link=]]</div> |
| | | | |
| − | Time to live maximum for RRsets and messages in the cache. Default is 86400 seconds (1 day). If the maximum kicks in, responses to clients still get decrementing TTLs based on the original (larger) values. When the internal TTL expires, the cache item has expired. Can be set lower to force the resolver to query for data often, and not trust (very large) TTL values.
| |
| | | | |
| | + | '''Regras''' |
| | + | /ip firewall nat |
| | + | add action=dst-nat chain=dstnat comment="SPEEDR - EXTERNO SSH" dst-port=2229 in-interface=\ |
| | + | ether1 protocol=tcp to-addresses=10.10.150.2 to-ports=2229 |
| | | | |
| − | max-udp-size: <number>
| + | __NOEDITSECTION__ |
| − | | + | [[Category:Teste]] |
| − | Maximum UDP response size (not applied to TCP response). 65536 disables the udp response size maximum, and uses the choice from the client, always. Suggested values are 512 to 4096. Default is 4096.
| |
| − | | |
| − | | |
| − | msg-cache-size: <number>
| |
| − | | |
| − | Number of bytes size of the message cache. Default is 4 megabytes. A plain number is in bytes, append 'k', 'm' or 'g' for kilobytes, megabytes or gigabytes (1024*1024 bytes in a megabyte).
| |
| − | | |
| − | | |
| − | num-queries-per-thread: <number>
| |
| − | | |
| − | The number of queries that every thread will service simultaneously. If more queries arrive that need servicing, and no queries can be jostled out (see jostle-timeout), then the queries are dropped. This forces the client to resend after a timeout; allowing the server time to work on the existing queries. Default depends on compile options, 512 or 1024.
| |
| − | | |
| − | | |
| − | delay-close: <msec>
| |
| − | | |
| − | Extra delay for timeouted UDP ports before they are closed, in msec. Default is 0, and that disables it. This prevents very delayed answer packets from the upstream (recursive) servers from bouncing against closed ports and setting off all sort of close-port counters, with eg. 1500 msec. When timeouts happen you need extra sockets, it checks the ID and remote IP of packets, and unwanted packets are added to the unwanted packet counter.
| |
| − | | |
| − | | |
| − | rrset-cache-slabs: <number>
| |
| − | | |
| − | Number of slabs in the RRset cache. Slabs reduce lock contention by threads. Must be set to a power of 2.
| |
| − | | |
| − | cache-min-ttl: <seconds>
| |
| − | | |
| − | Time to live minimum for RRsets and messages in the cache. Default is 0. If the minimum kicks in, the data is cached for longer than the domain owner intended, and thus less queries are made to look up the data. Zero makes sure the data in the cache is as the domain owner intended, higher values, especially more than an hour or so, can lead to trouble as the data in the cache does not match up with the actual data any more.
| |
| − | | |
| − | | |
| − | root-hints: <filename>
| |
| − | | |
| − | Read the root hints from this file. Default is nothing, using builtin hints for the IN class. The file has the format of zone files, with root nameserver names and addresses only. The default may become outdated, when servers change, therefore it is good practice to use a root-hints file.
| |
| − | | |
| − | | |
| − | auto-trust-anchor-file: <filename>
| |
| − | | |
| − | File with trust anchor for one zone, which is tracked with RFC5011 probes. The probes are several times per month, thus the machine must be online frequently. The initial file can be one with contents as described in trust-anchor-file. The file is written to when the anchor is updated, so the unbound user must have write permission. Write permission to the file, but also to the directory it is in (to create a temporary file, which is necessary to deal with filesystem full events).
| |
| − | | |
| − | | |
| − | prefetch: <yes or no>
| |
| − | | |
| − | If yes, message cache elements are prefetched before they expire to keep the cache up to date. Default is no. Turning it on gives about 10 percent more traffic and load on the machine, but popular items do not expire from the cache.
| |
| − | | |
| − | | |
| − | prefetch-key: <yes or no>
| |
| − | | |
| − | If yes, fetch the DNSKEYs earlier in the validation process, when a DS record is encountered. This lowers the latency of requests. It does use a little more CPU. Also if the cache is set to 0, it is no use. Default is no.
| |
![]() )
)
![]() )
)